Cybersecurity Games
Test Your Knowledge With CyberIQ Games
Turn traditional training on its head with GLS’s CyberIQ mini-games designed to motivate your employees with engaging and fun challenges. Our cybersecurity games provide a fresh alternative for your security awareness program and drive higher employee productivity and knowledge retention with short, impactful training exercises.
Make our cybersecurity games part of your workplace training now.
Does the thought of another annual training cycle make you cringe? The countless reminders, the groans, the complaining. Training industry research shows that gamification has many positive effects on employee training, with 87% of employees saying it makes them more productive at work.
Imagine your employees using game-based training and they are excited about doing it. Employees will finish the cybersecurity games training with a sense of accomplishment that helps foster the behavior needed to reduce security risk in your organization.
Our cybersecurity games series offers the following features
- Test overall security awareness
- Receive important feedback on IQ challenge activities covering core cybersecurity topics
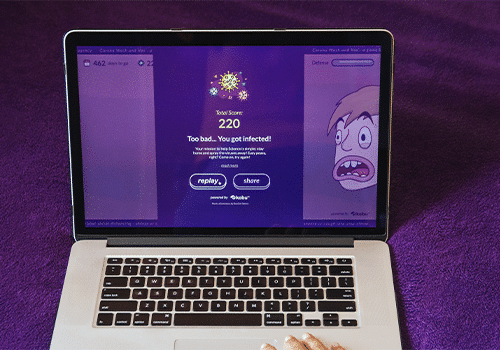
- Receive a personal CyberIQ score in less than five minutes

Benefits of Cybersecurity Games
Results and Insights
The IQ games serve as learning assessments for both the individual user and the organization to identify potential knowledge gaps and risk areas that require additional reinforcement training.
Engaging Activities
A successful training strategy is one that removes the “dread” of long, non-interactive training in addition to fostering individual responsibility, competition and camaraderie among your employees.
Return on investment
Employees enjoy the game-based, IQ challenge format; retain the knowledge received; and foster a security mindset in the organization – reducing your organization’s risk and saving you thousands of dollars.
Results and Insights
The IQ games serve as learning assessments for both the individual user and the organization to identify potential knowledge gaps and risk areas that require additional reinforcement training.
Engaging Activities
A successful training strategy is one that removes the “dread” of long, non-interactive training in addition to fostering individual responsibility, competition and camaraderie among your employees.
Return on investment
Employees enjoy the game-based, IQ challenge format; retain the knowledge received; and foster a security mindset in the organization – reducing your organization’s risk and saving you thousands of dollars.
Featured Article
How Gamification Increases Engagement
Gamification in security awareness training has gained popularity in recent years as a motivational strategy. Gamified courses may utilize points, leaderboards, badges, puzzles, scenarios and timing rewards. They all share a common goal: to make training more engaging and fun while simultaneously promoting learning.
Program Setup and Monitoring
Cybersecurity Games Topics
- CyberIQ Challenge
- Data Protection IQ Challenge
- Passwords and Authentication IQ Challenge
- Phishing IQ Challenge
- Remote Work IQ Challenge

Fill out the form below to contact us!