Cybersecurity Awareness Challenge


Course Description
Cybercrime is rising rapidly on a global scale and affecting millions of organizations, big and small. Experts warn that costs in fighting this threat could reach $10.5 trillion annually by 2025. Human error continues to be the biggest threat to information security. The training content we offer to your employees and contractors is the first step in fighting the major impact cybercrime has on personal information.
As an introduction to our cybersecurity awareness training programs, this course aims to reduce human error by teaching how to secure remote and home offices, ensure mobile security, avoid social engineering scams such as pretexting and phishing attacks, as well as create strong passwords to protect personal data and avoid data breaches. The Cybersecurity Awareness Challenge engages users by describing real-life security challenges and asking them to choose the best course of action for each challenge. This course is a recent update to course 5826 and includes a final 8-question quiz.
- Topic
- Security Awareness
- Learning Modality
- Courseware
- Role/Audience
- All Employees
- Language
- 20+ Languages
- Total Time
- 25 Minutes

The Cybersecurity Awareness Challenge course:
- Is created for any organization that is required to deliver annual security training and/or that seeks to strengthen and enhance their company’s overall security posture
- Provides relevant information on all common aspects of information security
- Engages learners in hands-on problem-solving using case study-based examples
- Addresses the key concepts behind classifying and handling sensitive data, recognizing insider threats, creating strong passwords, securing mobile devices, and recognizing and avoiding phishing threats
Course Curriculum
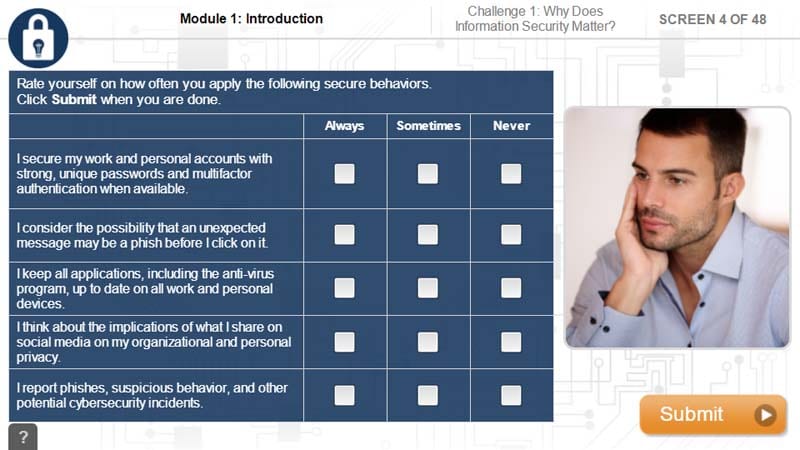
Module 1: Introduction
- Communicates the need for a strong information security program and the consequences of not having one
Module 2: Data Classification and Protection
- Explains the importance of classifying data correctly and using strong passwords — and also how to handle, share and protect data from unauthorized disclosure and insider threat
Module 3: Mobile and Remote Office Security
- Teaches how to protect secure data when using mobile devices and working from home or a remote office
Module 4: Social Engineering
- Describes common social engineering tactics, such as phishing, baiting, quid pro quo and tailgating — and provides best practices to avoid becoming a victim
Module 5: Final Reminders
- Reinforces the importance of information security and how organizational employees are the best line of defense against cyberattacks
Quiz
- Tests the user’s knowledge via a scenario-driven eight-question quiz
Upon completion, learners will be able to:
- Describe the importance of information security
- Understand the impact of their personal security habits
- Apply best practices for handling and sharing sensitive data
- Understand how to create strong passwords
- Recognize the red flags associated with insider threats
- Implement best practices for protecting mobile devices and the data in them
- Improve the security of data they handle when working from home
- Recognize social engineering threats such as phishing, pretexting, baiting, quid pro quo and tailgating
- Follow universal best practices for avoiding social engineering threats and ransomware attacks
Request a Demo or Quote
Please complete the form below and a GLS representative will contact you



