2017 was a huge year for email phishing. We saw a 4x increase in spam emails, a consistent increase in phishing rates in every quarter of 2017, and an increase of almost 900% in W-2 phishing emails. None of these statistics, however, represents the most nerve-racking development of 2017: the rise of cloud phishing. Our most trusted applications are now being used to hijack our information.
Out of all the SAAS products cloud phishing scams that have come up this year, the ones from Oauth are some of the most prominent. “Oauth” is a simple protocol designed to allow you to sign on to many accounts with one protocol—just click “Sign in with Facebook” or “Sign in with Google” and instantly gain access to any new app. This new method of gaining access seems to have benefited everyone involved: users can now effortlessly get into apps, and applications have gained greater credibility and security by partnering themselves with battle-tested firewalls like Google.
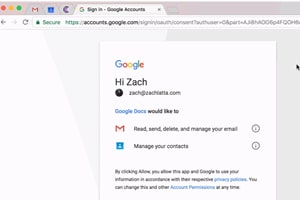
But there’s a problem: in an attempt to spread their “Sign in with [our service]” buttons across the web, Oauth providers stopped scrupulously vetting the third party applications they were helping authenticate. What resulted is a brand-new breed of phishing scams: difficult to detect, highly effective, and capable of tricking even very technical employees.That’s because these phishing scams look like this:
Take a look at the page above. The url is correct, the browser is using extended-validation SSL, and the application requesting access is “Google Docs”. But make no mistake: this page is part of a phishing scam. And it is capable of accessing not just the information above—email history and contacts—but also google drive, google photos, or even location & search history…simply by requesting access as a “trusted” provider.
This type of SAAS products phishing is not going away. In fact, it’s only going to expand: every major application we use on a daily basis—Facebook, Slack, Salesforce, Zendesk, and even Amazon—is now vulnerable to these kinds of attacks. Get a user to click an Oauth link, and you can steal all the information your heart desires. Let’s face it: phishing in 2018 is going to get a lot trickier. Major scams like the aforementioned Google Docs will continue and get more sophisticated.
Additionally, this new breed of attacks is posing great risk to traditional intrusion-prevention systems by rendering traditional methods of detection useless. For instance, most intrusion-detection systems today use DNS “greylisting” to find scams. Endpoint protection tools and network-level systems then prevent users from connecting to untrusted DNS names. But with an Oauth attack, all data is being accessed through Google.com. As soon as you grant permission, the cloud platform—not your network—is sending out your data. To combat this type of phishing attack—aside from the essential step of training employees—organizations can implement Cloud Access Security Brokers (CASBs) such as Netskope, Bitglass, and Saviynt. CASBs monitor and defend against cloud application data access by refining permissions across the cloud. While not foolproof, these types of systems will play an essential role in the phishing landscape in 2018. Keep Users Safe from Phishing Attacks
What Can You Do?
GLS knows that your employees’ cybersecurity awareness should not stop when they leave the office at the end of a workday. The principles they learn as part of their training at work should be extended to protecting personal data so that good habits are practiced 24×7 to reinforce positive behaviors and prevent phishing attempts.
As part of our Human Firewall 2.0 program, Global Learning Systems offers courses for prevention of online scams in: