Anti-Phishing Essentials Course

Course Description
Phishing scams come in many forms, targeting weaknesses in humans and technology across organizations and networks. A successful attack can expose data, spread malware infections or give access to restricted systems. Phishing attacks can occur through email, SMS texting, phone calls and social media in an attempt to steal sensitive data.
Phishing has become the weapon of choice for cybercriminals. It’s important to be vigilant to prevent attacks, as they can have severe consequences. The Colonial Pipeline attack in 2021, for example, temporarily shut down the pipeline supplying gas to the entire eastern coast of the United States. The incident created a panic for businesses and individuals alike.
GLS’s anti-phishing essentials course teaches how to avoid becoming a victim of phishing attacks by explaining how phishing attacks work and how to recognize email phishing, which accounts for approximately 70% of cyberattacks worldwide.
With a variety of gamified cyber training and phishing simulations, this award-winning cybersecurity training course has been the product of choice for leading global-based organizations. It provides real-world scenarios to identify and avoid ransomware attacks on personal information.
- Topic
- Anti-Phishing
- Learning Modality
- Courseware
- Role/Audience
- All Employees
- Language
- 8+ Languages
- Total Time
- 20 Minutes

Anti-Phishing Essentials is perfect for any organization, large or small, that needs in-depth anti-phishing training and/or seeks to strengthen and enhance their company’s overall security and risk mitigation posture. This gamified training program provides:
- Relevant information on all common types of phishing exploits
- Hands-on problem-solving using case-study-based examples
- A proven solution that targets learners at all levels of the organization. Using GLS’ success-based learning design through Tier challenges, this program effectively engages in-attentive employees and habitual repeat clickers within your organization.
Course Curriculum
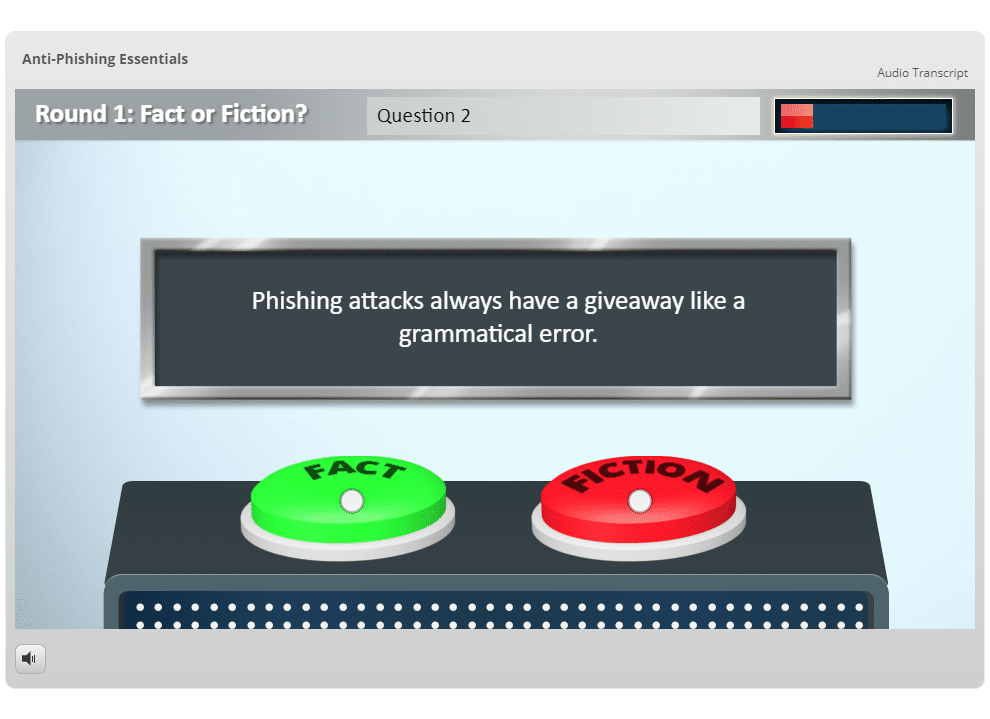
- Uses a gameshow format to bust common phishing myths
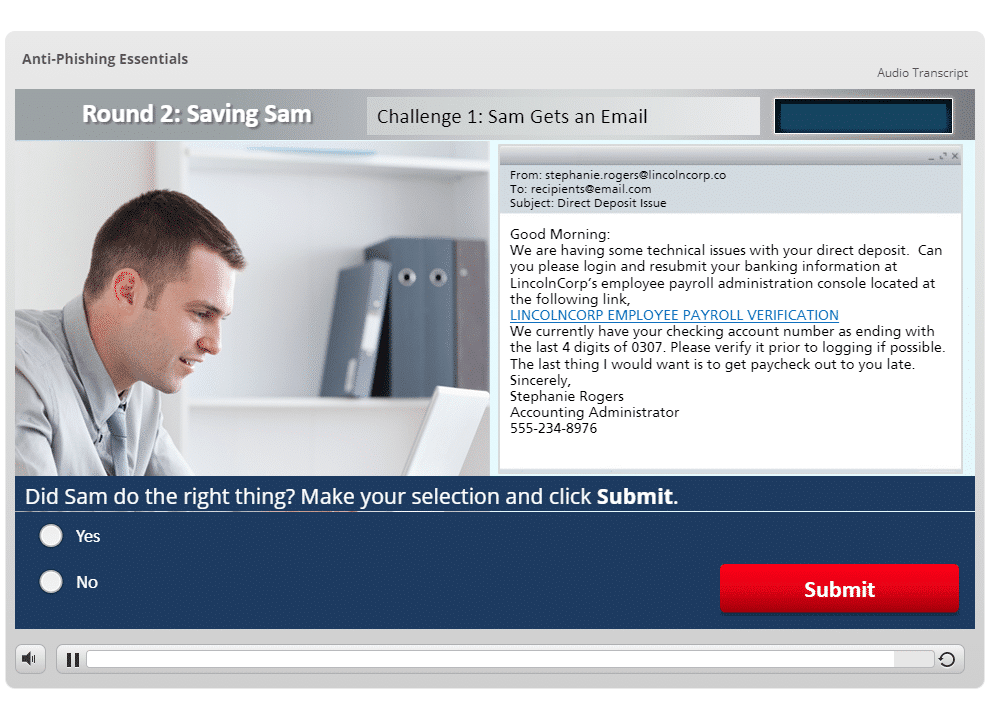
- Explores the inbox of an average employee named Sam to educate users on how phishing scams work, the different forms that phishing can take (including ransomware attacks, spear phishing, BEC attacks, and text and social media messages), how to recognize a phishing message, and what basic steps to take to avoid becoming a victim
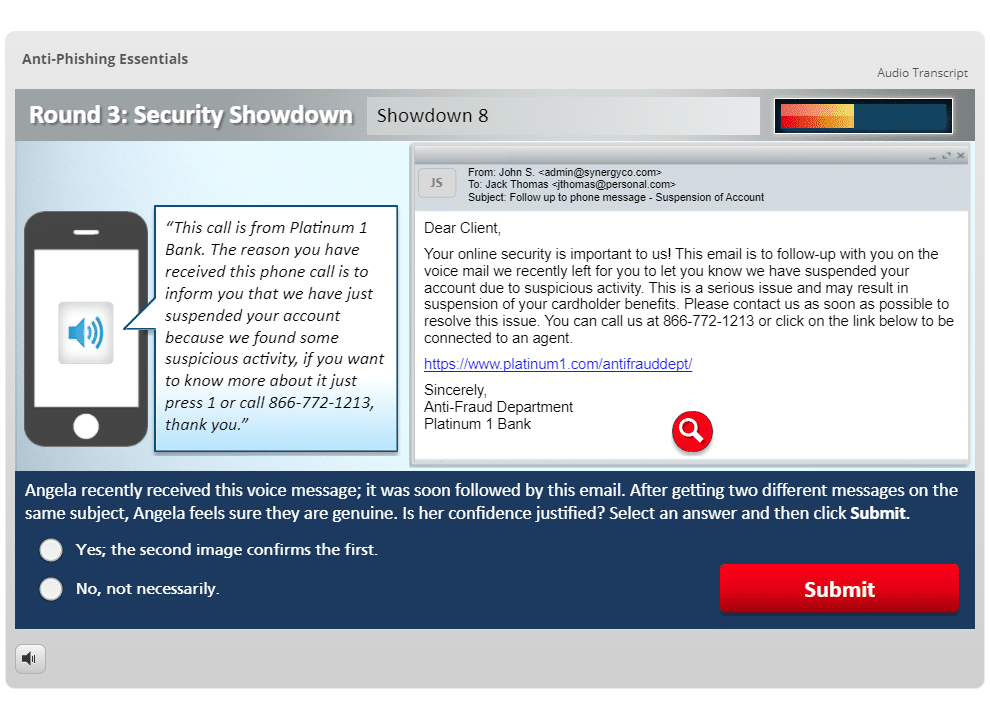
- The final round tests the user’s knowledge of phishing by presenting an eight-question scenario-based quiz
Upon completion, learners will be able to:
- Distinguish between phishing facts and myths
- Define phishing and its risks to an organization
- Describe how phishing attacks are carried out
- Recognize specific characteristics of suspicious emails and websites
- Identify web links and suspicious URLs
- List strategies for how to avoid getting phished
Get anti-phishing training from GLS
Please complete the form below and a GLS representative will contact you



